

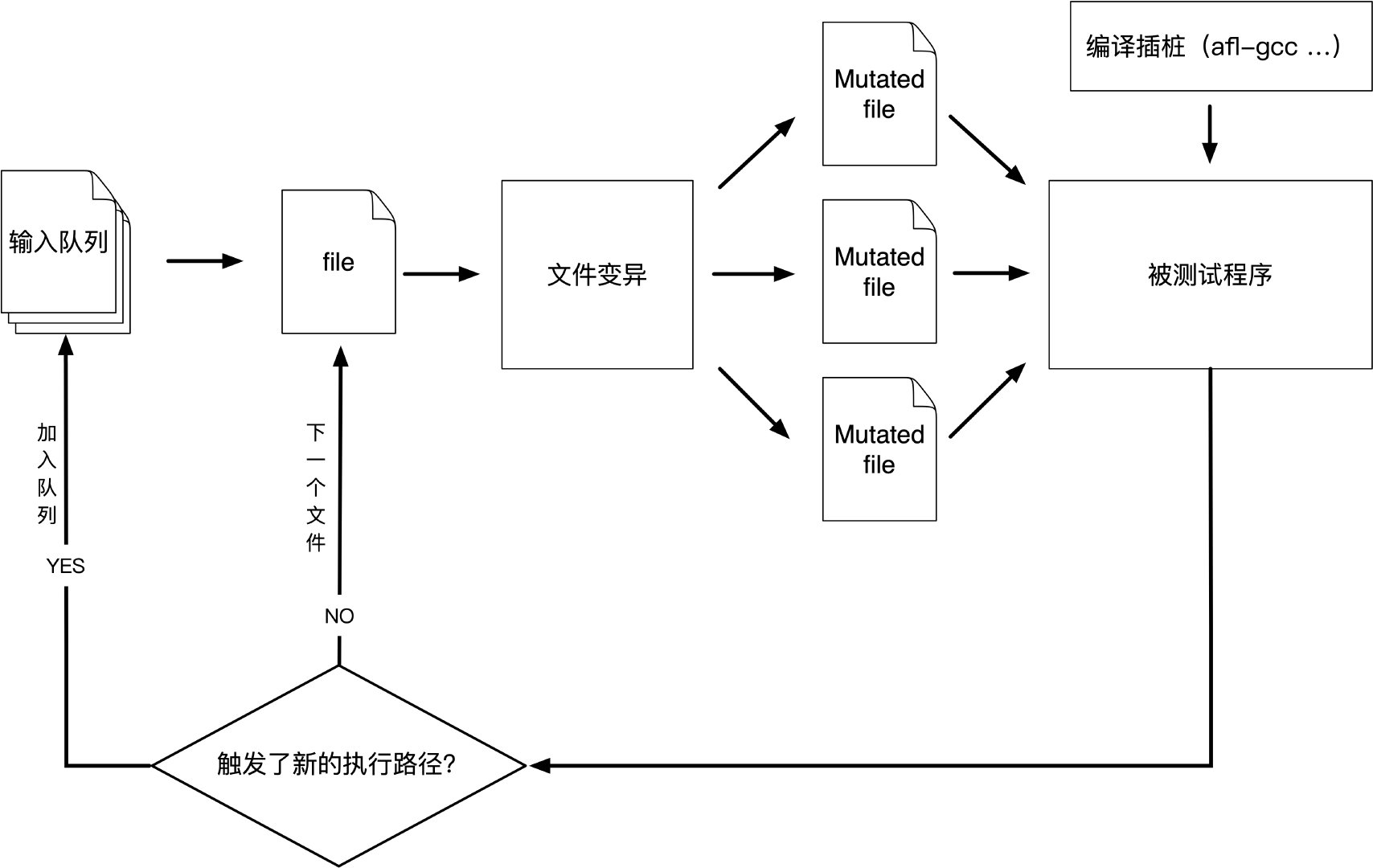
AFL(American Fuzzy Lop),由Michał Zalewski开发的基于覆盖引导的模糊测试工具
通过记录输入样本的代码覆盖率,从而调整输入样本以提高覆盖率,增加发现漏洞的概率
http://lcamtuf.coredump.cx/afl/
wget http://lcamtuf.coredump.cx/afl/releases/afl-latest.tgz
tar zxvf afl-latest.tgz
cd afl-2.52b
make
make install
cd afl-2.52b/qemu_mode
apt install libtool-bin
apt install bison
./build_qemu_support.sh
glibc>=2.27会报错
util/memfd.c:40:12: error: static declaration of ‘memfd_create’ follows non-static declaration
static int memfd_create(const char *name, unsigned int flags)
解决方案
https://xz.aliyun.com/t/2805
https://github.com/abiondo/afl
TODO
cd afl-2.52b/libtokencap
make
make install
cd afl-2.52b/libdislocator
make
make install
afl-gcc gcc的封装
afl-g++ g++的封装
afl-clang clang的封装
afl-clang++ clang++的封装
afl-fuzz 对目标程序进行fuzz
afl-analyze 对用例进行分析
afl-plot 生成测试任务的状态图
afl-tmin 对用例进行简化,将单个输入文件进行压缩
afl-cmin 对用例进行简化,给出输入数据的最小集合
afl-whatsup 查看测试任务的状态
afl-gotcpu 查看当前CPU的状态
afl-showmap 对单个用例进行执行路径跟踪
查看当前CPU的状态
afl-gotcpu
afl-gotcpu 2.52b by <lcamtuf@google.com>
[*] Measuring per-core preemption rate (this will take 1.00 sec)...
Core #2: AVAILABLE
Core #3: AVAILABLE
Core #0: AVAILABLE
Core #1: CAUTION (111%)
>>> PASS: You can run more processes on 3 to 4 cores. <<<
对用例进行分析
afl-analyze 2.52b by <lcamtuf@google.com>
afl-analyze [ options ] -- /path/to/target_app [ ... ]
Required parameters:
-i file - input test case to be analyzed by the tool
Execution control settings:
-f file - input file read by the tested program (stdin)
-t msec - timeout for each run (1000 ms)
-m megs - memory limit for child process (50 MB)
-Q - use binary-only instrumentation (QEMU mode)
Analysis settings:
-e - look for edge coverage only, ignore hit counts
For additional tips, please consult /usr/local/share/doc/afl/README.
afl-analyze -i ./fuzz_in/1 ./test
afl-analyze 2.52b by <lcamtuf@google.com>
[+] Read 1 byte from './fuzz_in/1'.
[*] Performing dry run (mem limit = 50 MB, timeout = 1000 ms)...
[*] Analyzing input file (this may take a while)...
01 - no-op block 01 - suspected length field
01 - superficial content 01 - suspected cksum or magic int
01 - critical stream 01 - suspected checksummed block
01 - "magic value" section
[000000] 1
[+] Analysis complete. Interesting bits: 0.00% of the input file.
[+] We're done here. Have a nice day!
###afl-cmin
对用例进行简化,给出输入数据的最小集合
corpus minimization tool for afl-fuzz by <lcamtuf@google.com>
Usage: /usr/local/bin/afl-cmin [ options ] -- /path/to/target_app [ ... ]
Required parameters:
-i dir - input directory with the starting corpus
-o dir - output directory for minimized files
Execution control settings:
-f file - location read by the fuzzed program (stdin)
-m megs - memory limit for child process (100 MB)
-t msec - run time limit for child process (none)
-Q - use binary-only instrumentation (QEMU mode)
Minimization settings:
-C - keep crashing inputs, reject everything else
-e - solve for edge coverage only, ignore hit counts
For additional tips, please consult docs/README.
afl-cmin -i fuzz_in -o output ./test
fuzz_in
wdnmd
2
fuck
output
2
对用例进行简化,将单个输入文件进行压缩
afl-tmin 2.52b by <lcamtuf@google.com>
afl-tmin [ options ] -- /path/to/target_app [ ... ]
Required parameters:
-i file - input test case to be shrunk by the tool
-o file - final output location for the minimized data
Execution control settings:
-f file - input file read by the tested program (stdin)
-t msec - timeout for each run (1000 ms)
-m megs - memory limit for child process (50 MB)
-Q - use binary-only instrumentation (QEMU mode)
Minimization settings:
-e - solve for edge coverage only, ignore hit counts
-x - treat non-zero exit codes as crashes
For additional tips, please consult /usr/local/share/doc/afl/README.
afl-tmin -i fuzz_in/1 -o outfile ./test
afl-tmin 2.52b by <lcamtuf@google.com>
[+] Read 370 bytes from 'fuzz_in/1'.
[*] Performing dry run (mem limit = 50 MB, timeout = 1000 ms)...
[+] Program exits with a signal, minimizing in crash mode.
[*] Stage #0: One-time block normalization...
[+] Block normalization complete, 370 bytes replaced.
[*] --- Pass #1 ---
[*] Stage #1: Removing blocks of data...
Block length = 32, remaining size = 370
Block length = 16, remaining size = 32
Block length = 8, remaining size = 32
Block length = 4, remaining size = 32
Block length = 2, remaining size = 28
Block length = 1, remaining size = 26
[+] Block removal complete, 345 bytes deleted.
[*] Stage #2: Minimizing symbols (1 code point)...
[+] Symbol minimization finished, 0 symbols (0 bytes) replaced.
[*] Stage #3: Character minimization...
[+] Character minimization done, 0 bytes replaced.
[*] --- Pass #2 ---
[*] Stage #1: Removing blocks of data...
Block length = 1, remaining size = 25
[+] Block removal complete, 0 bytes deleted.
File size reduced by : 93.24% (to 25 bytes)
Characters simplified : 1480.00%
Number of execs done : 121
Fruitless execs : path=13 crash=0 hang=0
[*] Writing output to 'outfile'...
[+] We're done here. Have a nice day!
1
aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa
outfile
0000000000000000000000000
对单个用例进行执行路径跟踪
afl-showmap 2.52b by <lcamtuf@google.com>
afl-showmap [ options ] -- /path/to/target_app [ ... ]
Required parameters:
-o file - file to write the trace data to
Execution control settings:
-t msec - timeout for each run (none)
-m megs - memory limit for child process (50 MB)
-Q - use binary-only instrumentation (QEMU mode)
Other settings:
-q - sink program's output and don't show messages
-e - show edge coverage only, ignore hit counts
-c - allow core dumps
This tool displays raw tuple data captured by AFL instrumentation.
For additional help, consult /usr/local/share/doc/afl/README.
afl-showmap -o output ./test
output
019522:1
对目标程序进行fuzz
afl-fuzz 2.52b by <lcamtuf@google.com>
afl-fuzz: invalid option -- 'h'
afl-fuzz [ options ] -- /path/to/fuzzed_app [ ... ]
Required parameters:
-i dir - input directory with test cases
-o dir - output directory for fuzzer findings
Execution control settings:
-f file - location read by the fuzzed program (stdin)
-t msec - timeout for each run (auto-scaled, 50-1000 ms)
-m megs - memory limit for child process (50 MB)
-Q - use binary-only instrumentation (QEMU mode)
Fuzzing behavior settings:
-d - quick & dirty mode (skips deterministic steps)
-n - fuzz without instrumentation (dumb mode)
-x dir - optional fuzzer dictionary (see README)
Other stuff:
-T text - text banner to show on the screen
-M / -S id - distributed mode (see parallel_fuzzing.txt)
-C - crash exploration mode (the peruvian rabbit thing)
For additional tips, please consult /usr/local/share/doc/afl/README.
#include <stdio.h>
#include <stdlib.h>
#include <signal.h>
int main(int argc, char const *argv[])
{
char buf[20];
gets(buf);//栈溢出
if(buf[0] == 'a' & buf[1] == 'b')//前两字节为'ab',crash
{
raise(SIGSEGV);
}
printf("Hello World!");
return 0;
}
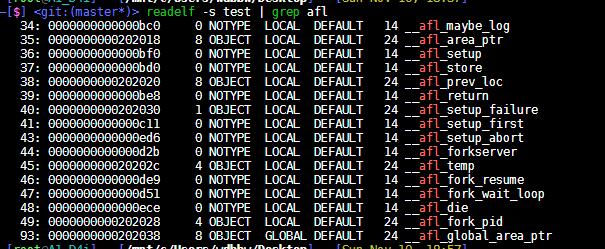
用afl-gcc编译
afl-gcc -g -o test test.c
编译后会有插桩
开始fuzz
fuzz_in文件夹中是测试用例,不能为空
放入一个写有字符串’1’的文件
afl-fuzz -i ./fuzz_in -o ./fuzz_out ./test
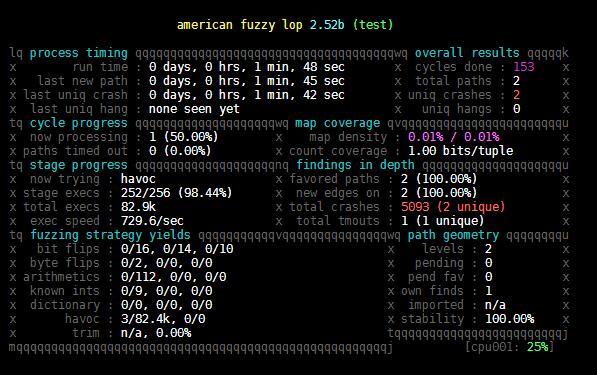
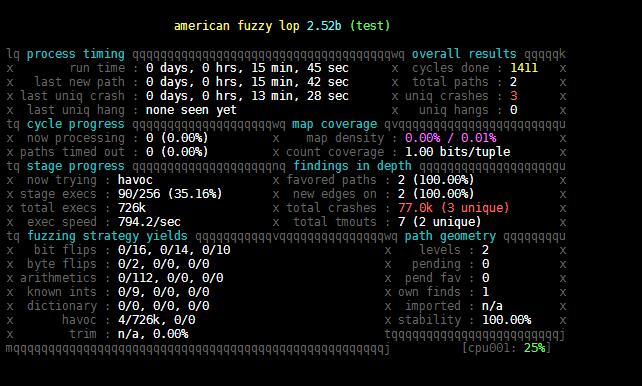
Process timing:运行总时长,距离最近的新路径、crash、hang的时间
Overall results:状态概述
Cycle progress:输入队列的进度
Map coverage:代码覆盖相关
Stage progress:正在执行的变异策略、执行次数和执行速度
Findings in depth:路径信息、crash和hang总数
Fuzzing strategy yields:变异策略产生的结果
Path geometry:执行路径的信息
CPU load:CPU利用率
fuzz_out文件夹
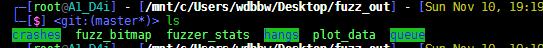
queue
文件夹包含每个独特执行路径的测试用例,第一个是给出的起始文件
1
a
hangs
hangs文件夹包含导致测试程序超时的测试用例
crashes
文件夹包含导致测试程序崩溃的测试用例,里面的README.txt保存了目标执行这些crash文件的命令行参数
跑出来3个crash
abaLaaaaa@aa
前两字节为’ab’
aamaWaaaaaaaaaaaaaaaaaaLaaaaaaaaaaaaaWaaaaaaaa
栈溢出
1818 0066 f2f2 f2f2 f2db 0000 1818 0060
1866 f2f2 f2f2 f2db 0000 8018 0060 1ae8
4318 b80b 50ff 1850 00e8 4318 b818 50ff
1850 0000 8080
栈溢出
fuzzer_stats
afl-fuzz的运行状态
start_time : 1573462573
last_update : 1573462995
fuzzer_pid : 19948
cycles_done : 304
execs_done : 296735
execs_per_sec : 693.43
paths_total : 4
paths_favored : 2
paths_found : 1
paths_imported : 0
max_depth : 2
cur_path : 3
pending_favs : 0
pending_total : 0
variable_paths : 0
stability : 100.00%
bitmap_cvg : 0.01%
unique_crashes : 3
unique_hangs : 0
last_path : 1573462574
last_crash : 1573462581
last_hang : 0
execs_since_crash : 291078
exec_timeout : 20
afl_banner : test
afl_version : 2.52b
target_mode : default
command_line : afl-fuzz -i fuzz_in -o fuzz_out ./test
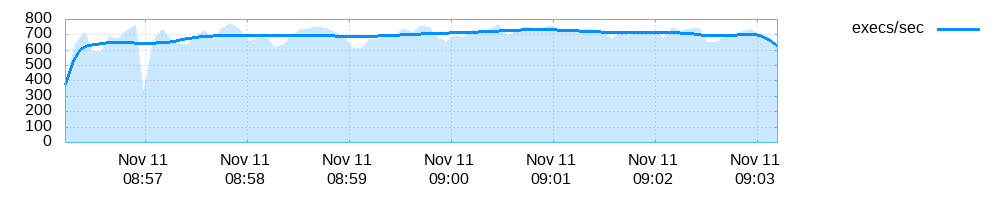
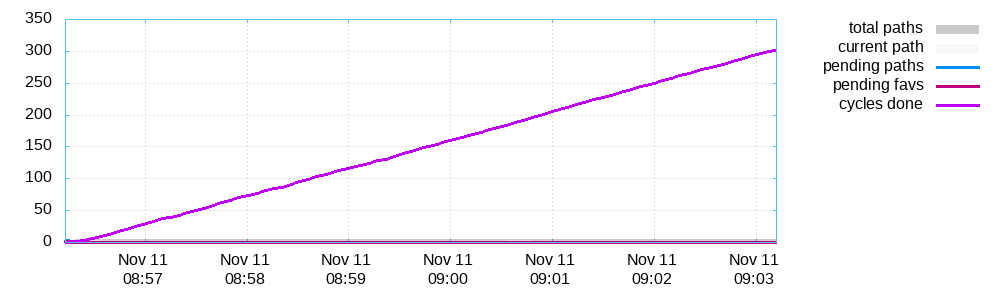
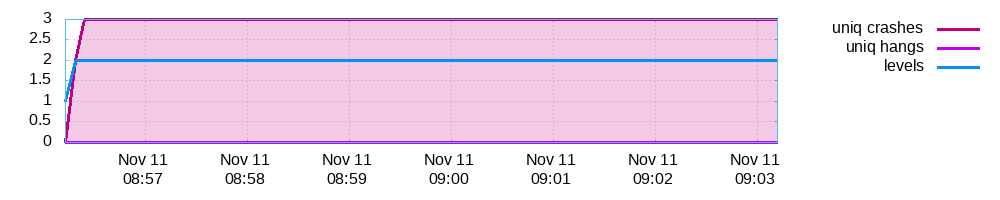
plot_data
afl-plot绘图
查看测试任务的状态
status check tool for afl-fuzz by <lcamtuf@google.com>
Usage: /usr/local/bin/afl-whatsup [ -s ] afl_sync_dir
The -s option causes the tool to skip all the per-fuzzer trivia and show
just the summary results. See docs/parallel_fuzzing.txt for additional tips.
读fuzz_out中的fuzzer_stats显示状态
不能直接使用fuzz_out目录
afl-whatsup fuzz_out
status check tool for afl-fuzz by <lcamtuf@google.com>
[-] Error: parameter is an individual output directory, not a sync dir.
把fuzzer_stats取出来
afl-whatsup stats
status check tool for afl-fuzz by <lcamtuf@google.com>
Individual fuzzers
==================
>>> test (0 days, 1 hrs) <<<
Instance is dead or running remotely, skipping.
Summary stats
=============
Fuzzers alive : 0
Dead or remote : 1 (excluded from stats)
Total run time : 0 days, 0 hours
Total execs : 0 million
Cumulative speed : 0 execs/sec
Pending paths : 0 faves, 0 total
Crashes found : 0 locally unique
progress plotting utility for afl-fuzz by <lcamtuf@google.com>
This program generates gnuplot images from afl-fuzz output data. Usage:
/usr/local/bin/afl-plot afl_state_dir graph_output_dir
The afl_state_dir parameter should point to an existing state directory for any
active or stopped instance of afl-fuzz; while graph_output_dir should point to
an empty directory where this tool can write the resulting plots to.
The program will put index.html and three PNG images in the output directory;
you should be able to view it with any web browser of your choice.
根据plot_data画图
afl-plot fuzz_out/ out
本作品采用知识共享署名-非商业性使用-禁止演绎 4.0 国际许可协议(CC BY-NC-ND 4.0)进行许可。
This work is licensed under the Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License (CC BY-NC-ND 4.0).